Are you prepared to defend your data against the hidden threats of the digital world? Cybersecurity is more critical than ever as sophisticated attacks evolve, targeting individuals and organizations alike. From AI-powered scams to social engineering tactics, today’s digital landscape demands vigilance. Dive in to discover how EchoStar’s cybersecurity teams stay one step ahead—and how you can protect yourself, too.
Every year during Cybersecurity Awareness Month, a time dedicated to raising awareness about the importance of protecting digital spaces. For our Information Security (InfoSec) team, this is not just a month but a core part of their mission year-round. Key leaders of the InfoSec team, Jim Adkins, Vice President of Information Security and Chele Sylvester, Manager of Security Governance, shared their insights into the teams they lead and the role they play in keeping EchoStar secure.
The InfoSec team is a multi-functional unit with specialized areas, each responsible for a unique aspect of cybersecurity. This team is in charge of implementing and maintaining “security controls,” which are the protective mechanisms that shield our systems from threats. These controls include firewalls, email security filters, multi-factor authentication, file integrity monitoring and partnerships with cybersecurity companies. The team also scans software code to identify and resolve vulnerabilities, partnering closely with development teams to enhance security at every stage.
The InfoSec team also ensures that the entire organization meets necessary security standards and policies. Chele plays a central role in cybersecurity awareness activities, working to promote secure practices, and making sure all departments understand and follow security protocols. Jim leads the InfoSec team through a cycle of continuous improvement, regularly assessing and refining our security policies, architecture and operations to stay ahead of emerging threats.
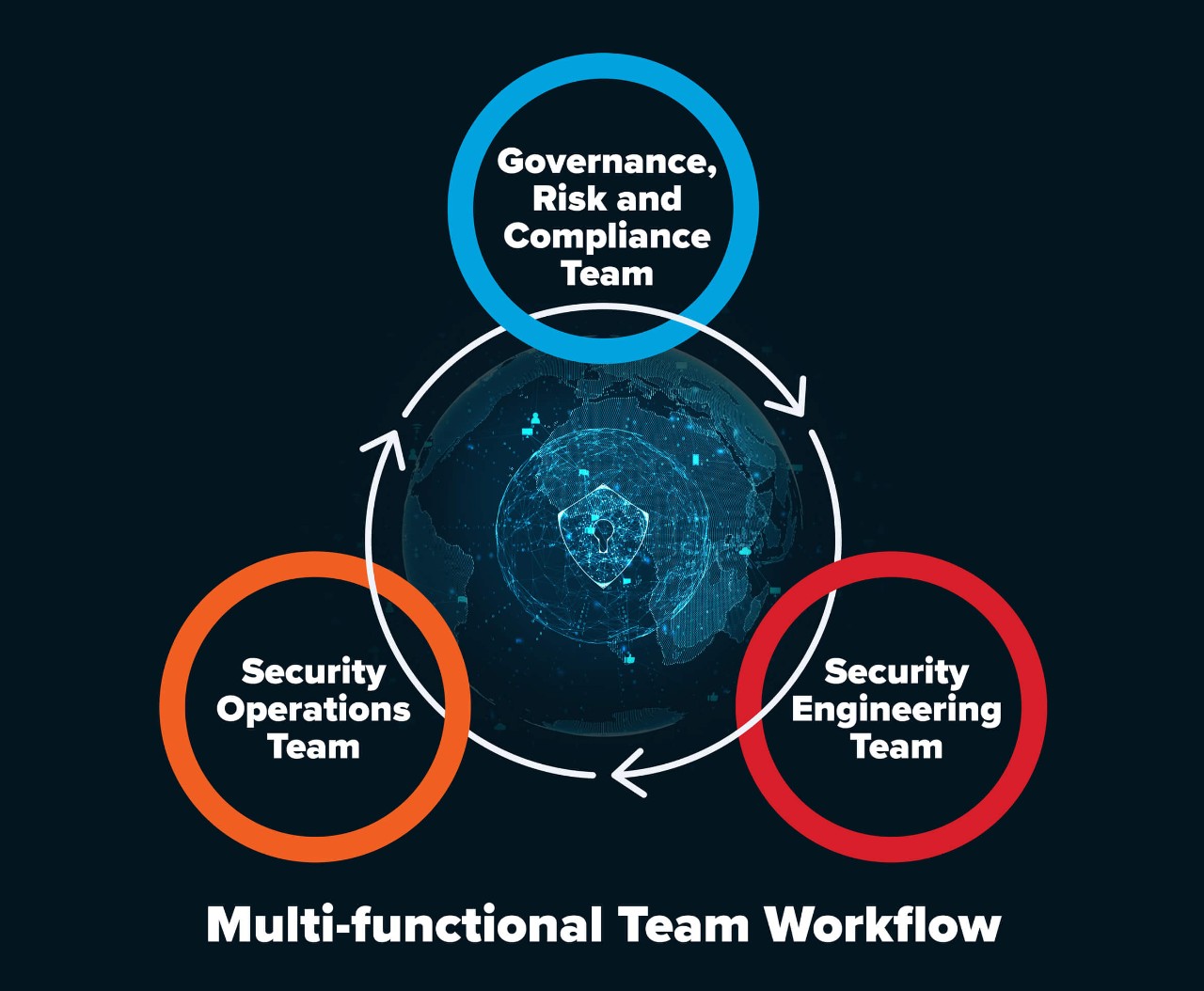
InfoSec’s Governance, Risk and Compliance (GRC) team begins this cycle by establishing security requirements. These are evaluated and passed on to the Security Engineering team, which determines the best way to implement and monitor them. Operations then steps in, keeping an eye on any unusual activity and responding to potential threats. If gaps are identified, they loop back with the GRC team to reassess requirements and strengthen security controls. This approach ensures an ongoing improvement cycle where every layer of security is constantly refined.